Continuous Deployment Strategies in High-Velocity Engineering Teams
Modern product teams are under constant pressure to ship faster without sacrificing stability. As platforms scale and user expectations tighten, continuous deployment strategies have moved from being a competitive advantage to an operational necessity. Teams are no longer debating whether to deploy frequently, but how to do so without increasing risk.
When people ask what is continuous deployment strategy, they are rarely looking for a definition. They want to understand how mature teams release changes continuously while protecting customers, revenue, and brand trust. In practice, a continuous deployment strategy is the set of technical and organisational decisions that allow every validated change to reach production safely and predictably.
Why Continuous Deployment Has Become Non-Negotiable
Speed Without Control Is a Liability
Shipping fast is easy; shipping fast safely is not. High-velocity teams face compressed release cycles, multiple daily deployments, and globally distributed users. Without a clear deployment strategy, speed quickly turns into instability, operational noise, and firefighting.
This is where modern deployment thinking differs from earlier DevOps adoption. Teams are no longer optimising for pipeline throughput alone, but for controlled exposure, fast recovery, and consistent user experience under constant change.
Reliability and User Experience Are Now Coupled
Every production change is a user-facing event, whether visible or not. Poor deployment practices manifest as degraded performance, partial outages, or inconsistent behaviour across regions. Mature continuous deployment strategies treat reliability and user experience as first-class constraints, not downstream concerns.
This shift aligns closely with broader architectural decisions discussed in areas like cloud platform selection and scalability trade-offs, explored in TheCodeV’s analysis of modern infrastructure choices:
https://thecodev.co.uk/cloud-providers-comparison-2025/
Continuous Deployment as a Strategic System
Beyond Pipelines and Tooling
A continuous deployment strategy is not a toolchain or a pipeline configuration. It is a system of branching decisions, release controls, runtime safeguards, and organisational discipline. The strategy defines how risk is managed incrementally, rather than deferred to large release events.
For engineering leaders, this means deployment strategy becomes a board-level concern. Downtime, regressions, and slow recovery directly impact growth metrics, retention, and customer trust. These outcomes cannot be solved by automation alone.
Aligning Engineering With Business Outcomes
At scale, deployment decisions influence cost efficiency, compliance posture, and incident response maturity. Teams that invest early in structured deployment strategies consistently outperform those relying on ad-hoc release practices. This is especially true for organisations delivering complex digital products and platforms as part of broader service engagements.
Many of these delivery considerations are embedded within TheCodeV’s end-to-end engineering and delivery approach across its core service offerings:
https://thecodev.co.uk/services/
Setting the Stage for Modern Deployment Patterns
Continuous deployment strategies provide the foundation for advanced release patterns such as canary releases, blue-green deployments, and feature flag-driven rollouts. These approaches are not interchangeable tactics, but responses to specific risk profiles, system architectures, and organisational maturity levels.
Understanding why continuous deployment matters at a strategic level is the first step. The next challenge is designing branching and release models that support this ambition without slowing teams down.
Branching Models That Enable Continuous Deployment at Scale
Branching strategy is where many continuous deployment initiatives quietly fail. Teams invest in automation and testing, yet still block themselves with long-lived branches and delayed merges. A continuous deployment branching strategy must reduce friction, not introduce new coordination overhead.
At scale, the branch model becomes a control surface for risk, speed, and collaboration. The wrong structure slows feedback, increases merge conflicts, and pushes risk downstream. The right one allows teams to deploy continuously without destabilising production.
Why Traditional GitFlow Breaks Continuous Deployment
GitFlow was designed for scheduled releases, not continuous ones. Long-lived development and release branches create artificial batching of change. By the time code reaches production, context is lost and rollback becomes expensive.
For teams shipping multiple times per day, GitFlow introduces avoidable delays. Every additional branch layer increases integration risk and hides defects until late in the cycle. This directly contradicts the goals of a continuous deployment strategy, where small, reversible changes are preferred.
Many organisations encounter this friction when modernising legacy systems or scaling engineering teams. Similar structural bottlenecks are discussed in TheCodeV’s breakdown of architectural evolution in complex systems:
https://thecodev.co.uk/shifting-from-monolith-to-microservices/
Trunk-Based Development as the Default
For most high-velocity teams, trunk-based development is the most effective branch strategy for continuous deployment. Engineers commit small, incremental changes directly to the main branch, often multiple times per day. Automated validation replaces manual gating.
This model works because it optimises for fast integration. Changes are merged while context is fresh, conflicts are smaller, and production always reflects the latest validated state. Risk is managed through testing, deployment controls, and runtime safeguards, not branch isolation.
Trunk-based development also aligns closely with modern cloud-native architectures. Stateless services, horizontal scaling, and fast rollback mechanisms reduce the need for branch-level safety nets.
Short-Lived Branches for Practical Flexibility
Pure trunk-based development is not always realistic. Complex features, regulated environments, or distributed teams may require temporary isolation. In these cases, short-lived branches provide flexibility without undermining deployment flow.
The key constraint is time. Branches should exist for hours or days, not weeks. The longer a branch lives, the more it accumulates risk and diverges from production reality. Successful teams enforce strict merge discipline and treat branch longevity as a measurable risk indicator.
This approach supports continuous deployment without sacrificing developer autonomy. It also allows teams to experiment safely while maintaining a stable mainline.
Release Branches as an Exception, Not a Rule
Release branches still have a place, but only under specific conditions. They are useful for supporting legacy versions, hotfixing critical production issues, or managing compliance-driven release approvals. However, they should not become the primary workflow.
In a mature continuous deployment strategy, release branches are tightly controlled and short-lived. They exist to stabilise a known state, not to accumulate new features. When overused, they signal deeper issues in testing, deployment confidence, or organisational trust.
Branching as a Strategic Decision
Choosing a continuous deployment branching strategy is not about developer preference. It is about aligning engineering flow with business expectations. Faster feedback loops reduce defects, accelerate learning, and improve user experience.
Teams delivering modern digital products increasingly treat branching as part of their delivery architecture. This perspective is common in organisations that engage in structured engineering delivery and platform design, such as those supported through TheCodeV’s software development services:
https://thecodev.co.uk/services/
With branching decisions in place, the next challenge is release execution. How changes are exposed to users determines whether continuous deployment feels safe or reckless. That is where release strategies like canary and blue-green deployments come into play.
Release Strategies That Make Continuous Deployment Safe
Branching enables flow, but release strategy determines risk. Once code reaches the mainline, teams still need a controlled way to expose changes to real users. A mature continuous deployment release strategy answers a simple question: how do we learn from production safely, without breaking trust?
At scale, release strategy is not an implementation detail. It is an operational contract between engineering, product, and users. The most effective approaches prioritise fast feedback, limited blast radius, and rapid recovery.
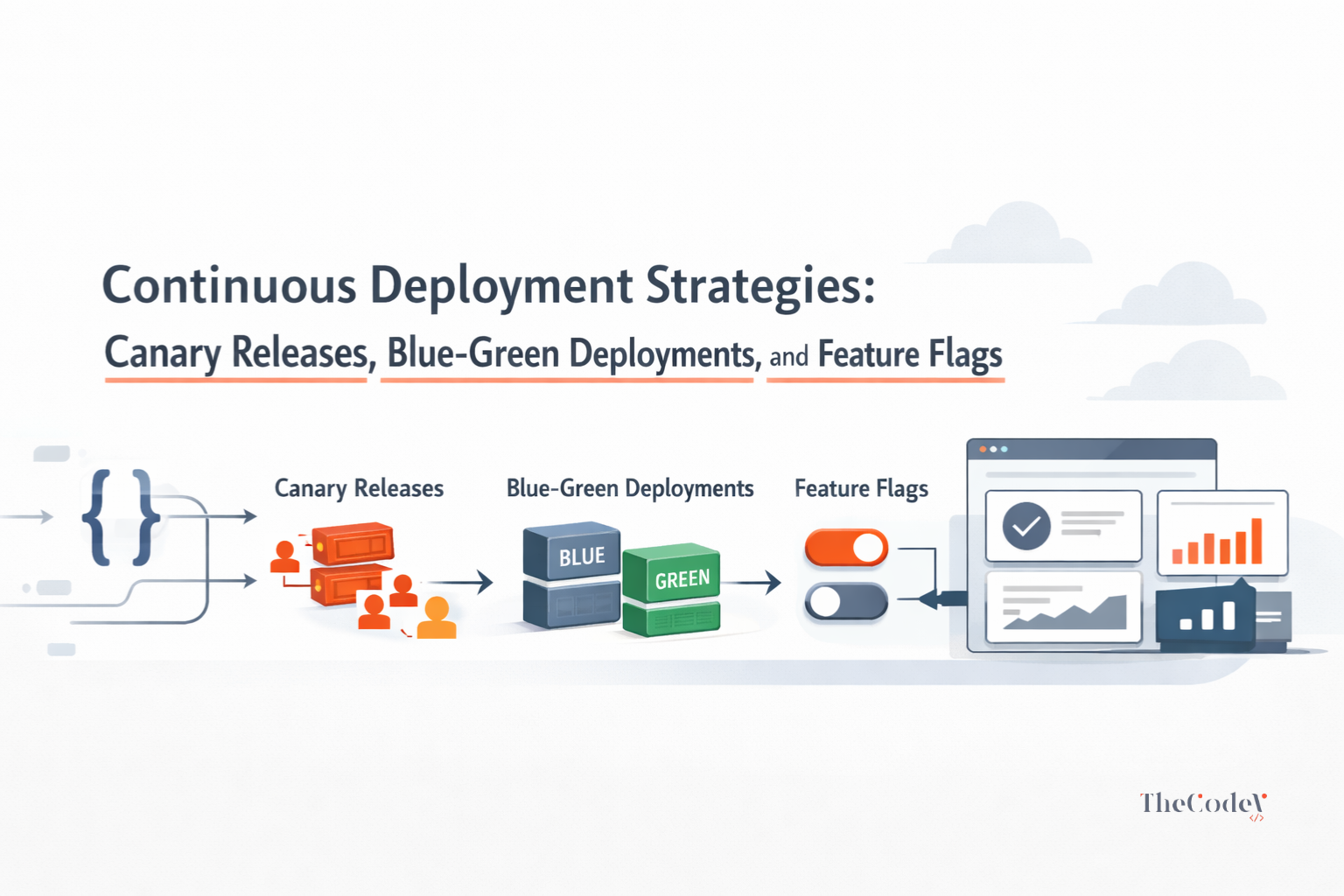
Canary Releases: Learning From a Small Audience First
Canary releases introduce changes to a small subset of users before wider rollout. This approach allows teams to observe real production behaviour under live traffic conditions. Performance regressions, error rates, and behavioural anomalies surface early, while impact remains contained.
The strength of canary releases lies in their feedback loop. Metrics, logs, and traces become decision signals rather than post-incident artefacts. When designed well, canaries turn production into a validation environment instead of a risk zone.
However, canaries require strong observability and automated decisioning. Without reliable signals, teams either overreact to noise or miss genuine issues. This dependency often exposes gaps in monitoring maturity and alert quality.
Blue-Green Deployments: Predictability and Fast Rollback
Blue-green deployments focus on environment-level isolation. Two production environments run in parallel, with traffic switching between them once validation completes. This model offers near-instant rollback by reverting traffic to the previous environment.
For systems with strict uptime requirements, blue-green deployments provide clarity and control. Releases become deterministic events rather than gradual experiments. This makes them popular in regulated industries and customer-facing platforms where predictability matters.
The trade-off is cost and complexity. Maintaining duplicate environments increases infrastructure spend and operational overhead. Teams must also ensure data compatibility between versions, especially when schema changes are involved.
Rolling Releases and Progressive Delivery
Rolling releases deploy changes incrementally across instances or regions. This approach balances speed and safety without requiring full environment duplication. When combined with health checks and automated rollback, rolling deployments provide steady exposure with minimal disruption.
Progressive delivery builds on this idea by integrating traffic shaping, segmentation, and automated analysis. Rather than deploying to everyone equally, teams control who sees what and when. This model aligns closely with modern cloud-native platforms and service meshes.
Cloud providers increasingly support these patterns natively. Google’s guidance on progressive delivery highlights how controlled exposure reduces risk while accelerating learning in production systems:
https://cloud.google.com/architecture/devops/devops-techniques-and-practices
Choosing the Right Release Strategy
No single release strategy fits every system. Canary releases favour learning and experimentation, blue-green deployments prioritise predictability, and rolling releases optimise for operational efficiency. The correct choice depends on traffic patterns, failure tolerance, and organisational maturity.
These decisions are closely tied to broader infrastructure and deployment architecture choices. TheCodeV explores similar trade-offs in its analysis of modern application runtime models:
https://thecodev.co.uk/serverless-vs-containerization/
Release Strategy as a Capability, Not a Tool
Release strategies are often mistaken for platform features. In reality, they are capabilities built from automation, observability, and operational discipline. Tools enable execution, but strategy determines outcome.
Teams delivering complex platforms and digital products increasingly treat release strategy as a first-class design concern. This mindset is embedded within TheCodeV’s approach to scalable software delivery across its engineering services:
https://thecodev.co.uk/services/
With release mechanics in place, the next constraint becomes confidence. Continuous deployment only works when teams trust their validation signals. That trust is built through a disciplined testing strategy designed for production reality, not pre-release comfort.
Testing as a First-Class Discipline in Continuous Deployment
In continuous deployment, testing is no longer a phase that happens before release. It is the mechanism that makes frequent production changes survivable. A strong continuous deployment test strategy shifts validation closer to real usage, where risk actually exists.
High-velocity teams accept that pre-production environments cannot fully model production behaviour. Instead of aiming for perfect prevention, they design tests to detect issues early, limit impact, and support fast recovery. This change in mindset is what separates scalable deployment from fragile automation.
Moving Beyond Test Coverage Metrics
Traditional testing strategies focus heavily on coverage and pass rates. While useful, these metrics say little about production safety. In continuous deployment, the more important question is whether tests provide reliable signals under real traffic conditions.
Effective teams prioritise contract tests, integration tests, and behaviour-driven checks that validate system boundaries. These tests catch breaking changes early without slowing delivery. Unit tests remain important, but they are no longer the primary safety net.
This approach aligns closely with modern distributed architectures, where failures often emerge from service interaction rather than isolated logic. The same architectural realities are explored in TheCodeV’s analysis of modern system design trade-offs:
https://thecodev.co.uk/serverless-vs-containerization/
Production Validation as a Testing Layer
One of the most significant shifts in continuous deployment strategy is accepting production as a validation environment. This does not mean experimenting recklessly with users. It means instrumenting systems so real behaviour informs deployment decisions.
Health checks, synthetic traffic, shadow requests, and real-time metrics act as continuous tests. They validate assumptions that cannot be proven in staging environments. When combined with controlled release strategies, production validation reduces unknown risk rather than increasing it.
Google’s engineering guidance consistently emphasises this model, particularly the role of observability and fast rollback in safe deployment practices:
https://sre.google/sre-book/monitoring-distributed-systems/
Automated Rollback and Decision Signals
Testing in continuous deployment is inseparable from rollback logic. A test that detects failure but cannot trigger recovery is incomplete. Mature teams define explicit success and failure thresholds tied to error rates, latency, and business metrics.
These thresholds turn deployment into a reversible decision rather than a one-way action. When signals degrade, automation responds faster than humans can. This reduces mean time to recovery and protects user experience during change.
Designing these feedback loops requires discipline and experience. It is one of the areas where structured engineering delivery frameworks provide significant leverage.
Testing Strategy as an Organisational Capability
A continuous deployment test strategy is not owned by QA alone. It spans engineering, operations, and product teams. Decisions about acceptable risk, monitoring depth, and rollback behaviour reflect organisational priorities as much as technical ones.
Teams that treat testing as a shared responsibility consistently deploy more often with fewer incidents. This mindset is common in organisations delivering complex digital systems through structured delivery models, such as those supported by TheCodeV’s software engineering services:
https://thecodev.co.uk/services/
With testing providing reliable signals, teams gain the confidence to decouple deployment from release. That separation is what enables advanced techniques like feature flags, which allow teams to control exposure without slowing delivery.
Feature Flags and Progressive Control in Continuous Deployment
As deployment frequency increases, control becomes more important than speed. Feature flags give teams the ability to deploy code independently from releasing functionality. In mature continuous deployment strategies, this separation is what allows rapid delivery without exposing users to unfinished or risky behaviour.
Rather than treating deployment as a binary event, feature flags introduce granularity. Teams can enable, disable, or segment functionality at runtime. This turns releases into controlled experiments instead of irreversible commitments.
Decoupling Deployment From Release
Traditional release models assume that deploying code means activating features. Feature flags break that assumption. Code can be merged, tested, and deployed continuously while remaining dormant in production until explicitly enabled.
This approach reduces merge pressure and shortens feedback loops. Engineers integrate work early, while product teams control when users actually see changes. For large teams, this coordination layer becomes essential to avoid bottlenecks and last-minute risk.
Feature flags also support safer branching models. When combined with trunk-based development, they reduce the need for long-lived branches by providing isolation at runtime rather than in source control.
Progressive Exposure and Risk Management
One of the strongest benefits of feature flags is progressive exposure. Features can be enabled for internal users, specific regions, or small user cohorts before wider rollout. This aligns closely with canary-style thinking, but operates at the feature level rather than the infrastructure level.
Progressive exposure limits blast radius and accelerates learning. Issues surface with real users under controlled conditions, allowing teams to react before full release. This improves both reliability and user experience, especially in complex products with diverse usage patterns.
These practices are particularly effective in modern cloud-native environments, where runtime configuration and dynamic routing are first-class capabilities. The same operational flexibility is discussed in TheCodeV’s exploration of cloud cost and control trade-offs:
https://thecodev.co.uk/cloud-cost-optimization-for-startups/
Managing Flag Debt and Operational Complexity
Feature flags introduce their own risks if left unmanaged. Flags that outlive their purpose increase cognitive load, complicate testing, and obscure system behaviour. Over time, this “flag debt” can undermine the clarity that continuous deployment relies on.
Mature teams treat flags as temporary by default. They define ownership, expiry expectations, and cleanup processes as part of their deployment discipline. Flags are reviewed and removed with the same intent as code.
Governance becomes especially important in regulated or high-availability systems. Without clear policies, flags can become hidden switches that bypass change control rather than enabling safe delivery.
Feature Flags as a Strategic Capability
Feature flags are often introduced tactically to solve immediate release pain. Over time, they evolve into a strategic capability that supports experimentation, resilience, and continuous improvement strategy deployment. When used deliberately, they enable teams to balance innovation with operational confidence.
This capability is most effective when embedded into a broader delivery framework that considers architecture, testing, and organisational flow together. Many teams adopt this holistic view when working within structured engineering models such as those delivered through TheCodeV’s software development services:
https://thecodev.co.uk/services/
With feature flags in place, teams gain fine-grained control over change. The remaining challenge is deciding which combination of branching, release strategy, and runtime control fits their product and risk profile. That decision requires a clear evaluation framework, which is addressed next.
Choosing the Right Continuous Deployment Strategy: A Practical Decision Framework
By this stage, it should be clear that no single approach defines a successful continuous deployment strategy. Effective teams assemble a combination of branching models, release techniques, testing signals, and runtime controls that match their context. The challenge is making these choices deliberately rather than inheriting them by accident.
A useful decision framework focuses less on tools and more on constraints. Product maturity, organisational structure, risk tolerance, and system architecture all shape what “good” looks like in practice. Teams that skip this evaluation often over-engineer solutions or adopt patterns they cannot sustain.
Start With Product and Business Risk
The first decision driver is business impact. Systems handling payments, healthcare data, or core revenue flows demand different controls than internal tools or early-stage products. High-risk domains benefit from predictable rollbacks and controlled exposure, making blue-green deployments or tightly governed canaries more appropriate.
Lower-risk products can optimise for learning speed. In these cases, trunk-based development combined with canary releases and feature flags often delivers faster iteration without meaningful downside. The key is aligning deployment risk with business consequence, not engineering preference.
This principle is closely tied to broader product and scaling decisions, similar to those outlined in TheCodeV’s analysis of common growth-stage technical missteps:
https://thecodev.co.uk/startup-scaling-mistakes-tech/
Evaluate Team Structure and Maturity
Team topology matters as much as architecture. Small, co-located teams can move quickly with minimal process. As teams grow, coordination costs increase and informal safeguards break down. Continuous deployment strategies must evolve accordingly.
Teams with strong automation culture and observability maturity can safely rely on progressive delivery and production signals. Less mature teams may require stricter release gates and simpler deployment patterns until confidence builds. A mismatch here often leads to brittle systems and deployment fatigue.
This is where external perspective can be valuable. Structured delivery models help teams adopt advanced practices at a sustainable pace, rather than forcing premature complexity.
Match Strategy to Architecture and Infrastructure
Architecture imposes hard limits on deployment choices. Monolithic systems often favour blue-green deployments for clarity and rollback speed. Distributed systems and microservices naturally align with canary releases and rolling deployments.
Infrastructure capability also plays a role. Cloud-native platforms make progressive delivery easier through native load balancing, traffic shaping, and monitoring. These trade-offs are explored further in TheCodeV’s comparison of modern runtime models and deployment environments:
https://thecodev.co.uk/serverless-vs-containerization/
Ignoring these constraints leads to fragile implementations that look good on diagrams but fail under load.
Balance Control With Operational Cost
Every deployment strategy carries cost. Duplicate environments increase spend, feature flags add governance overhead, and advanced observability requires investment. A sustainable continuous deployment strategy balances safety with operational efficiency.
Teams should explicitly decide where to spend complexity. For some, infrastructure duplication is acceptable. For others, fine-grained runtime control offers better leverage. What matters is that the trade-offs are visible and intentional.
Turning Strategy Into Execution
Choosing the right deployment approach is not a one-off decision. It is an evolving capability that matures alongside the product and organisation. Teams that revisit these choices regularly adapt faster and experience fewer large-scale failures.
This evaluative approach is central to how TheCodeV supports organisations in designing scalable delivery systems through its engineering and advisory services:
https://thecodev.co.uk/services/
https://thecodev.co.uk/consultation/
With a clear decision framework in place, teams can move beyond trial-and-error. The final step is embedding these strategies into day-to-day delivery in a way that builds trust, confidence, and long-term resilience.
Implementing Continuous Deployment Strategies With Confidence
Continuous deployment succeeds when it is treated as an operating model, not a collection of tactics. Teams that deploy confidently have aligned their branching approach, release strategy, testing signals, and runtime controls around a shared understanding of risk. This alignment is what allows frequent change without constant disruption.
At this stage, the question is no longer which techniques exist, but how they fit together in your environment. Canary releases, blue-green deployments, and feature flags each solve different problems. The strongest implementations combine them selectively, based on product criticality, team maturity, and architectural constraints.
From Patterns to Practice
Many organisations struggle not because they choose the wrong strategy, but because they implement it in isolation. Feature flags without governance create confusion. Canary releases without observability generate false confidence. Trunk-based development without discipline leads to instability.
Mature teams integrate these practices into a single delivery system. Deployment becomes a routine event, not a high-stakes moment. This consistency reduces cognitive load for engineers and builds trust across product, operations, and leadership.
The same principle appears repeatedly in high-performing engineering organisations: strategy first, tooling second. This systems-level thinking is also reflected in how modern teams approach cost, scalability, and operational control, as explored in TheCodeV’s guidance on sustainable cloud delivery models:
https://thecodev.co.uk/cloud-cost-optimization-for-startups/
Continuous Improvement Through Deployment
A well-designed continuous deployment strategy enables more than speed. It creates a feedback-rich environment where teams learn continuously from real usage. Small, frequent releases expose assumptions early and reduce the cost of being wrong.
Over time, this feedback loop drives better prioritisation, cleaner architecture, and more resilient systems. Deployment becomes a mechanism for improvement rather than a source of anxiety. This is where continuous improvement strategy deployment moves from theory into daily practice.
Organisations that reach this level rarely do so by accident. They invest deliberately in delivery design, technical governance, and team enablement.
When to Seek External Perspective
As systems grow, internal blind spots become harder to detect. Legacy decisions, organisational habits, and inherited constraints often limit progress. An external review can help teams reassess their deployment posture with fresh context and practical benchmarks.
This is especially valuable when scaling teams, modernising architecture, or increasing release frequency without increasing incident rates. Independent evaluation helps identify which controls add value and which create unnecessary friction.
TheCodeV supports organisations at this stage by helping them design and evolve deployment strategies that align engineering reality with business goals. These engagements focus on clarity, sustainability, and measurable improvement rather than adopting trends for their own sake.
If you are assessing how your current deployment approach supports growth, reliability, and user experience, a structured discussion can surface opportunities quickly. You can explore this further through TheCodeV’s consultation services:
https://thecodev.co.uk/consultation/
Building Deployment as a Long-Term Capability
Continuous deployment is not a destination. It is a capability that matures alongside your product and organisation. Teams that treat it as a strategic asset adapt faster, recover quicker, and deliver more confidently over time.
By grounding deployment decisions in risk, architecture, and user impact, organisations move beyond reactive releases. They build systems designed for change, not disrupted by it.